HA Background Information
Why Management High Availability?
The Security Management server includes several databases with information on the system, such as objects, users, and policy information. Every time the administrator makes changes to the system, this data changes. It is crucial to make a backup for this data, so that information is not lost in the event of a failure. If the Security Management server fails, or is down, a backup server needs to be in place to take over operations. If the primary Security Management (SmartCenter) server is down and there is no backup in place, operations by the Security Gateway, such as retrieval of the CRL, or fetching of the Security Policy cannot take place.
Security Management Server Backup
In Management High Availability, the Active Security Management server always has one, or more backup Standby Security Management servers that are ready to take over from the Active Security Management server, in case of failure. These must all be of the same OS and version (including HFAs and plug-ins).
The existence of the Standby Security Management server allows for backups to be in place:
- The database of objects and users, policy information and ICA files are stored on both the Standby Security Management server, as well as on the Active Security Management server. These are synchronized, so that data is maintained and ready to be used. If the Active Security Management server is down, a Standby Security Management server needs to become active, in order to be able to edit and install the Security Policy.
- Operations such as fetching a Security Policy, or retrieving a CRL can be performed on the Standby Security Management server.
Data Backed Up by the Standby Security Management Servers
For Management High Availability to function properly, the following data must be synchronized and backed up:
- Configuration and ICA data, such as:
- Databases (such as the Objects and Users)
- Certificate information, such as Certificate Authority data and the CRL that is available to be fetched by the Check Point Security Gateways
- The latest installed Security Policy. The installed Security Policy is the applied Security Policy. The Security Gateways must be able to fetch the latest Security Policy from either the Active or the Standby Security Management Server.
Synchronization Modes
There are two ways to perform synchronization:
- Manual synchronization is a process initialized by the system administrator. It can be set to synchronize Databases, or Databases and the installed Security Policy.
The former option synchronizes quicker than the latter option. It should be the preferred mode of synchronization, provided that the system administrator has edited the objects or the Security Policy, but has not installed the newly edited Security Policy, since the previous synchronization. - Automatic synchronization is a process configured by the system administrator to allow the Standby Security Management server to be synchronized with the Active Security Management server, at set intervals of time. This is generally the preferred mode of synchronization, since it keeps the Standby Security Management server updated. The basis for the synchronization schedule is that when the Security Policy is installed, both the installed Security Policy and all the databases are synchronized. Additionally, it is possible to synchronize the Standby Security Management servers when:
- The system administrator saves the Security Policy
- At a specified scheduled time
Even when automatic synchronization has been selected as the synchronization mode, it is possible to perform a manual synchronization.
Synchronization Status
The possible synchronization statuses are:
- Never been synchronized - immediately after the Secondary Security Management server has been installed it has not yet undergone the first manual synchronization that brings it up to date with the Primary Security Management server.
- Synchronized - the peer is properly synchronized and has the same database information and installed Security Policy
- Lagging - the peer Security Management Server has not been synchronized properly. For instance, on account of the fact that the Active Security Management Server has undergone changes since the previous synchronization (objects have been edited, or a Security Policy has been newly installed), the information on the Standby Security Management Server is lagging.
- Advanced - the peer Security Management Server is more up-to-date.
- Collision - the Active Security Management Server and its peer have different installed Security Policies and databases. The administrator must perform manual synchronization, and decide which of the Security Management Servers to overwrite.
Creating a Secondary Management Server
To create the Secondary Security Management Server:
- From the Menu, select Manage > Network Objects > Check Point > New > Host
- From Object Properties, under Network Policy Management, select Secondary Server.
- You will be prompted to specify whether it is the Primary Management or the Secondary Management. Select Secondary Management.
- Create a network object to represent the Secondary Security Management server:
- Select Manage > Network Objects > Check Point > New > Host
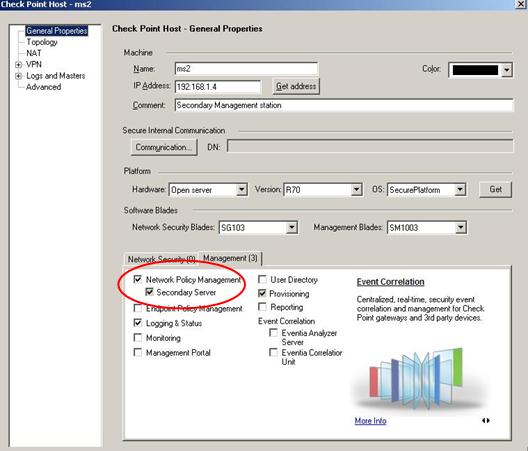
- In the Software Blades, section, select the Management tab, and select Secondary Server. Logging and Status will be selected automatically, as well.
- Initialize SIC between the Secondary Security Management server and the Primary Security Management server by selecting Communication.
- If a Security Gateway is installed on the Security Management server machine, install the policy first before doing a manual synchronization.
- Synchronize the Secondary Security Management server with the Active Security Management server by selecting: Policy > Management High Availability and then select Synchronize.
Putting the Active Management Server on Standby
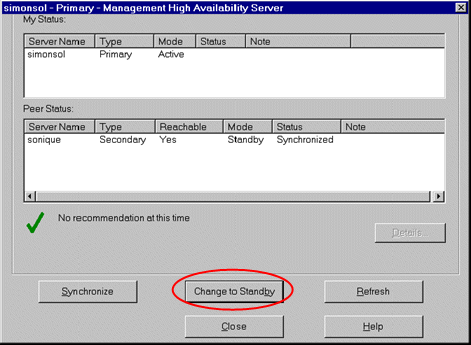
To change the Active Management Server to Standby:
- On the Active Security Management server, select Policy > Management High Availability to display the Management High Availability Server.
- In the displayed window, select Change to Standby.
Promoting the Standby Management Server to Active
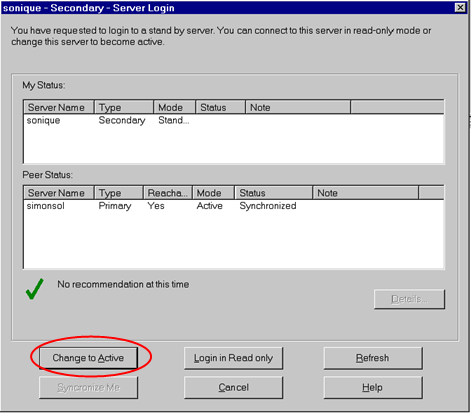
To change the Standby Management Server to Active:
- When logging in to the standby Security Management server, the Standby window is displayed.
- Select Change to Active.
Refreshing the Secondary Management Server Synchronization Status
The status of the Security Management server may have changed. You may decide to do a refresh.
To refresh the synchronization status of a Security Management server:
- Select Policy > Management High Availability to display the Management High Availability Servers window for the selected Security Management server.
- In the displayed window, select Refresh.
Selecting Synchronization Method
- The Policy > Global Properties - Management High Availability window defines the way in which the Standby Security Management server synchronizes with the Active Security Management server.
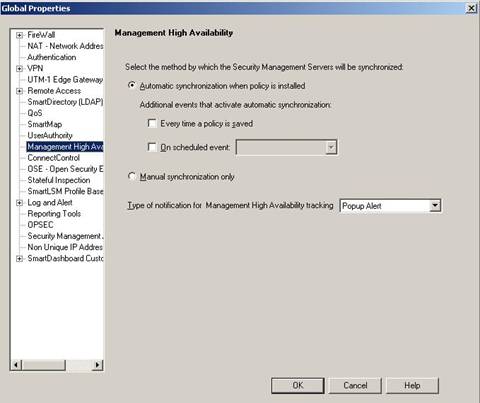
- The Secondary Security Management server can be synchronized automatically when the policy is saved / installed, or on a scheduled event. This can also be synchronized manually. If this is the chosen method, you will need to initiate it in the Management High Availability Servers window.
Tracking Management High Availability
To check the status of the Security Management servers:
- Select Policy > Management High Availability. This shows information about the Security Management server, which includes its peers - displayed with the name, status and type of Security Management server.
- All management HA operations can be seen in Audit Mode in SmartView Tracker.
Post a Comment